Suricata is an IDS/IPS engine. To build a complete solution, you will need to use other tools.
The following schema is a representation of a possible software setup in the case Suricata is used as IDS or IPS on the network. It only uses opensource components:
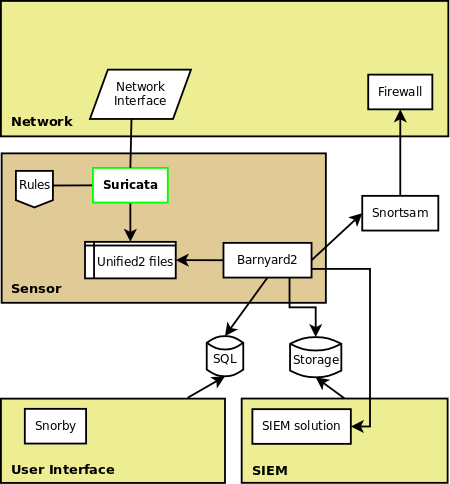
Suricata is used to sniff and analyse the traffic. To detect malicious traffic, it uses signatures (or rules). You can download a set of specialised rules from EmergingThreats.
To analyse the alerts generated by Suricata, you will need an interface such as, for example, snorby.
But this interface will need to have an access to the data. This is done by storing the alerts in a database. The feed of this database can be done by barnyard2 which take the files outputted by suricata in unified2 and convert and send them to a database (or to some other format).
If you want counter-measure to be taken (such as blocking for a moment attacker at the firewall level), you can use snortsam.
More complex setup can include interactions with a SIEM solution.