Objectives of this release
So it is my first ulogd2 release as maintainer. I’ve been in charge of the project since 2012 October 30th and this was an opportunity for me to increase my developments on the project. Roadmap was almost empty so I’ve decided to work on issues that were bothering me as a user of the project. I’ve also included two features which are connection tracking event filtering and a Graphite output module. Ulogd is available on Netfilter web site
Conntrack event filtering
When logging connections entries, there is potentially a lot of events. Filtering the events on network parameters is thus a good idea. This can now be done via a series of options:
- accept_src_filter: log only a connection if source ip of connection belong to the specified networks. This can be a list of network for example 192.168.1.0/24,1:2::/64
- accept_dst_filter: log only a connection if destination ip of connection belong to specified networks. This can be a list of networks too.
- accept_proto_filter: log only connection for the specified layer 4 protocol. It can be a list for example tcp,sctp
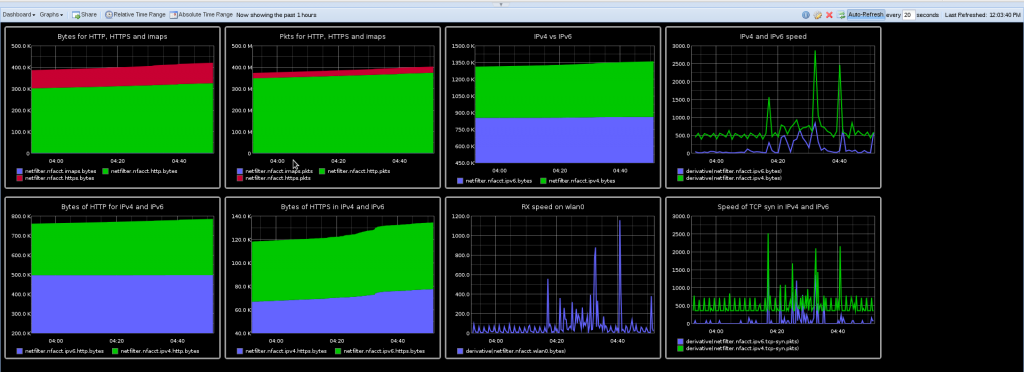
A GRAPHITE output module
This is the sexiest part of this release. Seth Hall from the Graphite, a scalable realtime graphing solution. I was playing at the moment with the new Netfilter accounting plugin of ulogd2 and my first thought has been that it was a good idea to add a new output ulogd2 plugin to export data to a Graphite server.
You can read more about Graphite output plugin on this dedicated post.
The result was really cool as show the following dashboard:
A better command line
In case of error, ulogd was just dying and telling you to read a log file. It is now possible to add the -v flag which will redirect the output to stdout and let you see what’s going one.
If it is to verbose for you, you can also set log level from command line via the -l option.
Improved build system
I’ve made some light improvement to the build system. First of all, a configuration status is printed at the end of configure. It displays the compiled input and output plugins:
Ulogd configuration:
Input plugins:
NFLOG plugin: yes
NFCT plugin: yes
NFACCT plugin: yes
Output plugins:
PCAP plugin: yes
PGSQL plugin: yes
MySQL plugin: yes
SQLITE3 plugin: no
DBI plugin: no
I’ve also added configure option to disable the building of some input plugins:
--enable-nflog Enable nflog module [default=yes]
--enable-nfct Enable nfct module [default=yes]
--enable-nfacct Enable nfacct module [default=yes]
For example, to disable Netfilter conntrack logging, you can use:
./configure --disable-nfct
.


