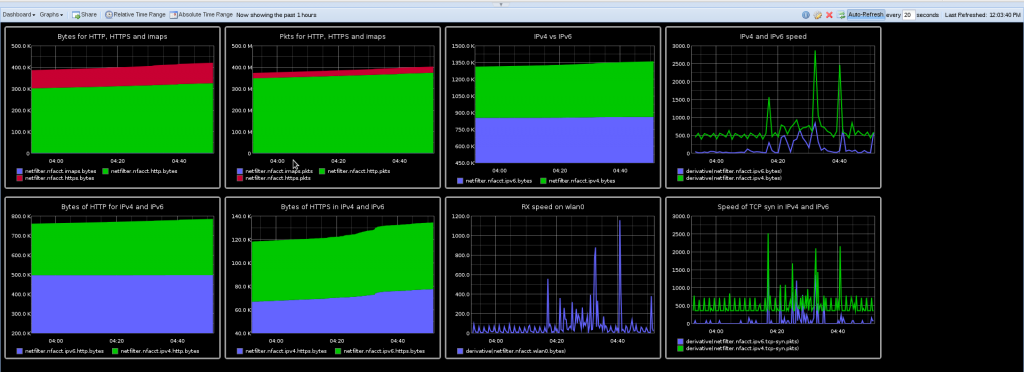
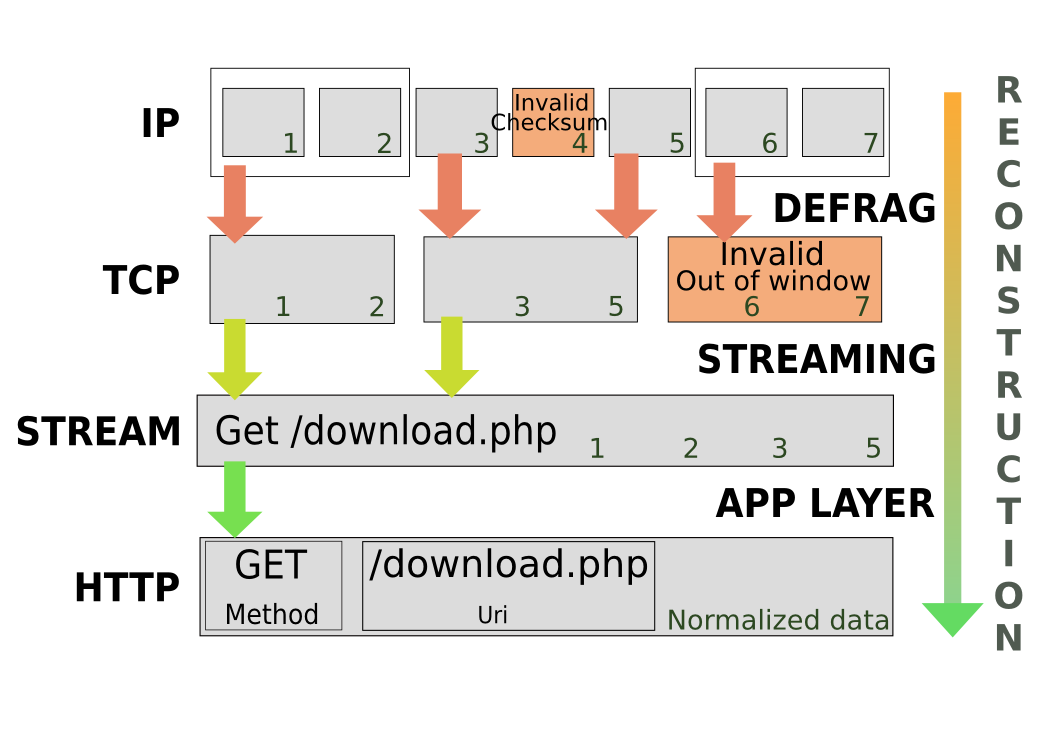
Introduction
Harald Welte when asked about IPv6 NAT was answering: “it will be over my dead body”. It is now available in official kernel.
Reasons for adding IPv6 NAT
- Dynamic IPv6 Prefixes : ISP assigning dynamic IPv6 prefixes so Internal network address change. NAT can bring you stability.
- Easier test setup.
- Users are asking and most operating systems have it.
To resume the arguments of NAT, Patrick McHardy used this video:
A single, clean, bug free implementation is better than a lot of incomplete non official implementations that where already available.
Release and implementation
It has been implemented in 2011 and merged in 2.6.37.
It is mainly based to on IPv4 implementation and provide from a user perspective a interface similar to IPv4.
It also features an implementation of RFC 6296: stateless network prefix translation. It operates on a packet base and is completely stateless.
It is implemented as an ip6tables target SNPT and DNPT which have to be used on both way to handle the modifications required by RFC 6296.
Current work
An implementation of NAT64 is currently in progress and should be available in the coming weeks.